Parrot 6.3: What’s New in the Latest Ethical Hacking OS?
What makes a cybersecurity tool stand out in a world full of digital threats? Constant updates and stronger features. Parrot 6.3 released brings major security upgrades, new hacking tools, and smoother performance. Designed for ethical hackers and IT teams, this version fixes past issues and adds tools to tackle modern cyberattacks. A recent study shows … Continue reading “Parrot 6.3: What’s New in the Latest Ethical Hacking OS?”


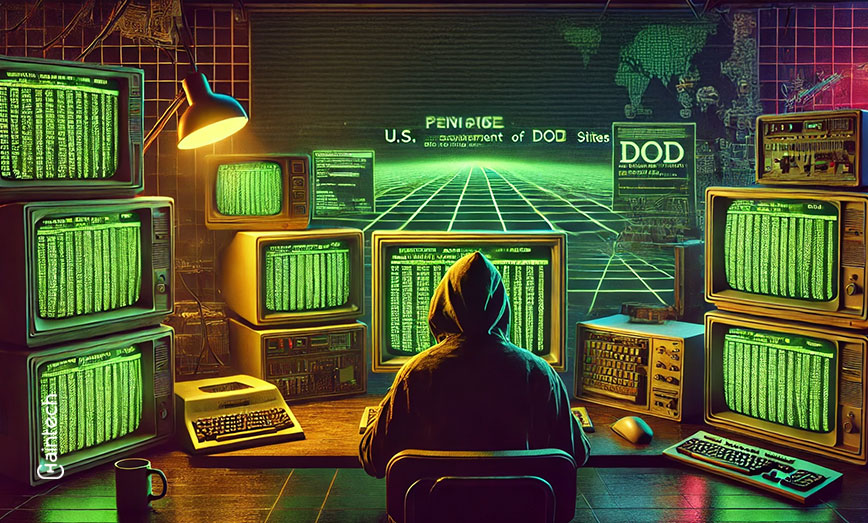
1990: Hackers from Netherlands Penetrated DoD Sites
Do you know who the first hackers were? Surprisingly, it was a group of Dutch hackers who, in 1990, managed to penetrate the computer networks of the United States Department of Defense. In fact, they successfully accessed some of the most sensitive yet unclassified military information. Interestingly, their actions exposed vulnerabilities that had long been … Continue reading “1990: Hackers from Netherlands Penetrated DoD Sites “

Year 1986: When WANK Worm Attacked Stanford University
Introduction Our previous blogs have been testimonials of all the major phreaking incidents that took place in the mid-1950s. It’s safe to say that many hackers’ journeys began with phone phreaking. Therefore, it’s reasonable to assume that phreaking played a role in the evolution of hacking. Phreaking, essentially the manipulation of telephone lines for personal … Continue reading “Year 1986: When WANK Worm Attacked Stanford University”


Year 1986: Chaos Computer Club Breaches German Government Computer; Exposes Chernobyl Data
Chernobyl & the Chaos Computer Club On the quiet night of April 26th, 1986, the city of Chernobyl slept peacefully until the sudden wailing of fire brigades woke them up. Looking outside their windows, the residents of Chernobyl saw a massive fire emerging from the Chernobyl Nuclear Power Plant. After several inquiries, the residents heard … Continue reading “Year 1986: Chaos Computer Club Breaches German Government Computer; Exposes Chernobyl Data”


Year 1984: The Hacking Marvels of Kevin Poulsen AKA “Dark Dante”
Introduction In our previous blog posts, we discussed about the lives of several renowned hackers and phone phreakers. We talked about figures like Joybubbles, John Draper, Steve Wozniak & Steve Jobs, and Kevin Mitnick, each leaving a significant mark on the world of hacking and phreaking. Today, we shift our focus to another notable individual … Continue reading “Year 1984: The Hacking Marvels of Kevin Poulsen AKA “Dark Dante””


Year 1983: Kevin Mitnick Gets Arrested For Illegally Accessing The ARPANET
Introduction Kevin Mitnick’s unparalleled hacking skills has cemented his status as one of the greatest hackers of all time, making him a focal point of our hacking series and sparking a wealth of captivating tales about his life. A legend in the hacking world, Mitnick earned the infamous title of “America’s Most Wanted Computer Outlaw” … Continue reading “Year 1983: Kevin Mitnick Gets Arrested For Illegally Accessing The ARPANET”


Year 1982: The U.S. Launches First Logic Bomb Attack on Russia
Introduction Wars have historically acted as catalysts for innovation in weaponry and military tactics, driving technological advancements at an accelerated pace. This was particularly evident during World War I and the Cold War between the United States and the Soviet Union. World War I marked a transition from 19th-century tactics to 20th-century technology. Armies adapted … Continue reading “Year 1982: The U.S. Launches First Logic Bomb Attack on Russia”


Year 1982: The Saga of Group “414”- Milwaukee Teenage Hackers
Introduction “Kids are curious.” And rightly so—curiosity is the mother of invention. As they grow, that curiosity only intensifies, especially when the world around them is on the brink of transformative change. Think of Professor Utonium from the Powerpuff Girls in his laboratory, diligently concocting his three beloved daughters. This scenario mirrors what occurs when … Continue reading “Year 1982: The Saga of Group “414”- Milwaukee Teenage Hackers”


Year 1981: The Hacking of Pacific Bell’s COSMOS Phone Centre
Introduction The early years of Kevin Mitnick have been nothing short of fascinating. From his humble beginnings as a hacker, phone phreaker, and social engineer, Mitnick’s journey has been filled with intrigue and controversy. While we’ve read about his infamous exploits in our previous blogs, today, we invite you to join us for yet another … Continue reading “Year 1981: The Hacking of Pacific Bell’s COSMOS Phone Centre”


Year 1981- The Fascinating Tale of Ian Murphy aka Captain Zap
Introduction If you’ve been following our hacking series since day 1, you likely didn’t anticipate the extent of cybercrime incidents, especially given the Internet’s early stages. But brace yourselves for some eye-opening statistics from the world of cybercrime. Currently, it’s a staggering $1.5 trillion industry, with a hacker attack occurring every 39 seconds on average, … Continue reading “Year 1981- The Fascinating Tale of Ian Murphy aka Captain Zap”




